
Security Advisory: Clock Fault Injection on Mocor OS – Password Bypass
Datum: 11.08.2023Autor: ONEKEY / CERTAINITY Reasearch Team
Introduction
This security advisory addresses a vulnerability discovered during a recent forensics engagement. Our investigation together with ONEKEY revealed that the Mocor OS, running on UNISOC SC6531E devices, is susceptible to a clock fault injection attack, which poses a significant threat to user data security and privacy. Through this attack vector, an unauthorized user with physical to a device access can bypass the device’s user lock, gaining unrestricted access to the main screen and compromising the integrity of the system. Notably, this vulnerability arises from a flaw in the soft reset routine performed by the OS kernel, which lacks proper permission checks for user passwords, making feature/burner phones vulnerable to exploitation.
Clock Glitching to bypass security lock
|
Affected vendor & product |
Mocor OS Tested on: o Spreadtrum SC6531E (Nemo G) devices o TCL, Nokia, Alcatel and more phones |
|
Vendor Advisory |
https://www.unisoc.com/en_us/secy/announcementDetail/1687281677639942145 |
|
Vulnerable version |
All versions |
|
Fixed version |
According
to UNISOC, this issue is fixed in the latest release of Mocor OS. |
|
CVE IDs |
|
|
Impact (CVSS) |
6.1 (Medium) CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N |
|
Credit |
ONEKEY & CERTAINITY Research Lab |
Description
Mocor OS is a proprietary operating system developed by UNISOC (Spreadtrum), a company known for producing mobile processors primarily for feature phones. This OS is widely adopted by various feature phone vendors, including well-known brands such as Nokia, TCL, Alcatel, and others. The specific vulnerability we have identified affects devices utilizing the UNISOC SC6531E chipset; however, it’s important to note that similar vulnerabilities might exist across other System-on-Chips (SoCs) as well.
The affected devices mainly include basic/burner phones that have been available in the market from 2017 to the present day. According to UNISOC, more than a billion chips have been sold to various vendors, including Nokia, TCL, and several other white-label phone manufacturers. This widespread adoption of the vulnerable chipset makes a substantial number of devices susceptible to the security flaw.
The nature of the vulnerability allows an attacker with physical access to exploit the device using a small metal wire, effectively bypassing the security lock and gaining unauthorized access to the device’s functions and data.
Steps to reproduce the security issue
- Mocor OS is vulnerable to a clock fault injection attack.
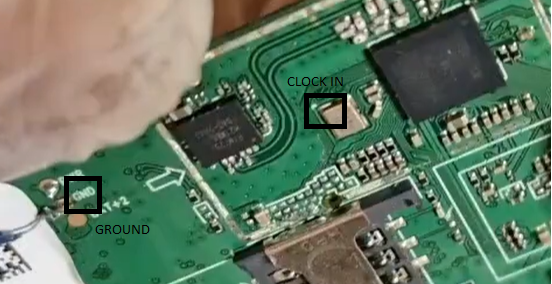
- To perform the attack, connect the CLK pin of the SoC to GND (ground) for a duration of 50-100 milliseconds.
- This action causes a crash of the Main OS, triggering a soft reboot by the SoC. However, during this soft reboot, certain permission checks that are normally performed during a regular reboot are bypassed.
- Exploit the vulnerability by injecting the fault precisely during the user-lock prompt at boot. This successful injection will result in the user-lock password being bypassed, providing the attacker with full access to the device.
The following video demonstrates exploitation of the vulnerability and a successful bypass of the password-protected user lock screen.
Key Takeaways
- Importance of proper error handling and fault injection mitigation:
- Rigorous checks for all paths leading to sensitive states:
- Avoidance of reliance on implicit assumptions:
- Limitations of feature/burner phones for storing high-sensitive information:
- Disposal of vulnerable devices containing sensitive information:
This vulnerability highlights the criticality of implementing robust error handling mechanisms and thoroughly addressing fault injection scenarios during software development. Proper validation and error checking at various stages can significantly enhance the security posture of the system.
Conducting comprehensive security assessments that thoroughly examine all possible paths leading to sensitive states is essential. Identifying and addressing vulnerabilities in such pathways can prevent potential exploitation and ensure the overall security of the system.
Relying on implicit assumptions about system behavior can lead to unforeseen security risks. It is vital to explicitly validate and verify all security-critical operations and not solely rely on assumed protections and execution paths to safeguard against potential attacks.
This vulnerability reinforces the fact that feature/burner phones are not designed to provide a high-level of security for sensitive information. Users should avoid relying solely on the device’s password prompt for data protection. Instead, opt for more secure devices and encryption mechanisms when handling sensitive data.
For users who possess vulnerable devices that contain sensitive information, it is advisable to erase and dispose of these devices if physical security is a part of their threat model. Proper disposal ensures that potential attackers cannot gain unauthorized access to sensitive data stored on these devices.
In summary, addressing this vulnerability demands a holistic approach to software development, incorporating rigorous security checks and mitigation measures to bolster system defenses. Additionally, users must exercise caution with regard to the types of devices used for sensitive data storage and be proactive in adopting more secure alternatives when needed.
Timeline
2023-03-30 – Contacting vendor through security@unisoc.com
2023-03-31 – Vendor responded and start analysis.
2023-05-25 – Vendor confirmed the vulnerability and working on fix.
2023-06-16 – Vendor requested one extra month to apply the patch.
2023-07-12 – Vendor contacted with the CVE for the vulnerability.
2023-08-05 – Vendor release the disclosure.
Reference
https://androidpctv.com/spreadtrum-sc6531-the-most-sold-soc-in-china-that-surely-you-didnt-know/
About ONEKEY
CERTAINITY and ONEKEY have established a valuable partnership and co-operate successfully. ONEKEY is a leading European specialist in Product Cybersecurity & Compliance Management. The unique combination of an automated Product Cybersecurity & Compliance Platform (PCCP) with expert knowledge and consulting services provides fast and comprehensive analysis, support and management to improve product cybersecurity and compliance from product purchasing, design, development, production to end-of-life. Critical vulnerabilities and compliance violations in device firmware are automatically identified in binary code by AI-based technology in minutes – without source code, device or network access. Proactively audit software supply chains with integrated software bill of materials (SBOM) generation. “Digital Cyber Twins” enable automated 24/7 post-release cybersecurity monitoring throughout the product lifecycle. Integrated compliance checking already covers the upcoming EU Cyber Resilience Act and existing requirements according to IEC62443-4-2, EN303645, UNR155 and many others. The Product Security Incident Response Team (PSIRT) is effectively supported by the integrated automatic prioritisation of vulnerabilities, significantly reducing the time to remediation. Leading international companies in Asia, Europe and the Americas already benefit from the ONEKEY Product Cybersecurity & Compliance Platform and ONEKEY Cybersecurity Experts.
