OSINT: How companies can benefit from open source intelligence
date: Sep 5, 2023author: Fabian Mittermair, Head of Offensive Security @ CERTAINITY
The term OSINT stands for “Open Source Intelligence” and refers to the systematic systematic collection and analysis of freely available information. These These freely accessible sources of information include, for example databases, social media, (dark net/deep web) websites, online blogs, but of course offline content such as magazines, books or company flyers. company flyers.
The use of The use of publicly available sources to obtain information has a very long history and was already used over 100 years ago by secret services, security security organizations and resourceful entrepreneurs to gain an information advantage. information advantage.
With the establishment of the Internet and global networking, the number of potentially available sources of information has exploded. Due to the advancing digitization and the easy availability of the corresponding technology unimaginable amounts of information can be processed automatically with little effort. be processed automatically with little effort. Under these conditions, OSINT has developed developed very strongly over the last 20 years. The use of OSINT data has never been as easy as it is today.
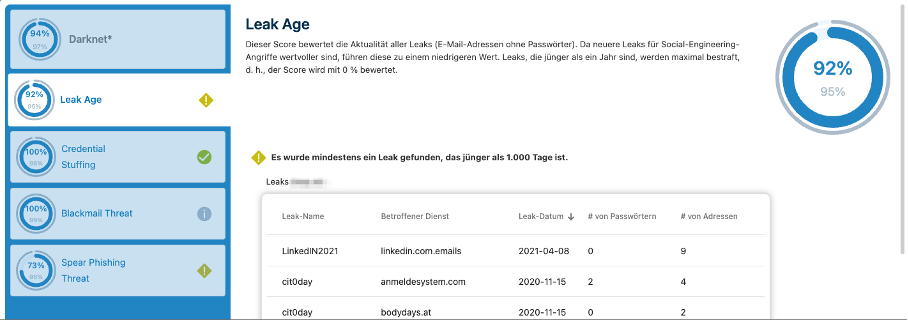
OSINT analysis of database leaks
Apart from the misuse of this information for targeted attacks on individuals and organizations individuals and organizations, it is possible to use the information to identify your own security risks and threats in advance and establish establish appropriate countermeasures. Every CIO/CISO/IT manager should should find out what information is freely available about their own company. company can be found.
What information does OSINT data contain?
Information that is collected collected and processed in the course of OSINT usually relates to individuals and organizations. Individuals and organizations. This includes personal data such as name, home address, date of birth and bank account number, but also personal preferences preferences, hobbies and behavioral patterns. In the case of organizations typically organizational charts, employee lists, financial and strategic information information or information about the technical IT infrastructure. This includes IP addresses, domains, software versions used, VPN access, DNS server configurations, backend logins or other IT platforms. IT platforms.
The true value of OSINT information only becomes apparent when the data is networked and correlations are and through the identification of correlations. For example combination of many individual pieces of publicly available information geographic movement profiles of trucks can be created. This information can then subsequently reveal the supply chains and intervals of a company. of a company. This networked information can then be used to the organization’s likely business strategy can be derived. This is just one example, but it shows how great the potential of networked information information can be.
Strengthen your own cyber defense with the use of OSINT
For the majority of currently visible cyber attacks are not highly complex and complicated attacks. complicated attacks. Cyber criminals like to take the path of least resistance resistance and act opportunistically. In the search for “good opportunities” systematically search for available sources of information (e.g. password leak files, …) are searched and network perimeters scanned. Based on this information, automated cyberattacks are then launched which, despite their can cause major damage despite their apparent triviality.
Furthermore OSINT data can also be misused to gather information about an organization’s employees. of an organization. Publicly accessible social networks, career websites or other public sources can be used for this purpose, to create a list of an organization’s employees, as well as to identify potential vulnerabilities in relation to social engineering attacks. identified.
One should be aware, however, that in addition to the benefits, there are also some limitations and challenges when using it. For example, data quality can vary greatly depending source and method. The information obtained can be incomplete or, in the worst case, incorrect. In addition may lead to ethical and legal issues when using certain information (e.g. data protection) or techniques (e.g. illegal procurement methods) can lead to ethical and legal challenges. legal challenges.
For companies and organizations organizations, it can therefore be well worth sifting through this information themselves and and keep an eye on known sources. Thanks to a range of - partly tools - some of which are free - it is now easy to keep an eye on a large to keep an eye on a large proportion of known sources. Through the use of OSINT data enables companies to recognize potential threats and security security gaps at an early stage. Apart from simple self research, companies such as CERTAINITY offer appropriate consulting services to consulting services to sustainably increase the security of their own IT systems. systems.
Conclusion
The use of OSINT is not only a valuable tool for cyber criminals, but also for entrepreneurs and a valuable tool and should be part of a sustainable cyber security strategy. of a sustainable cyber security strategy.
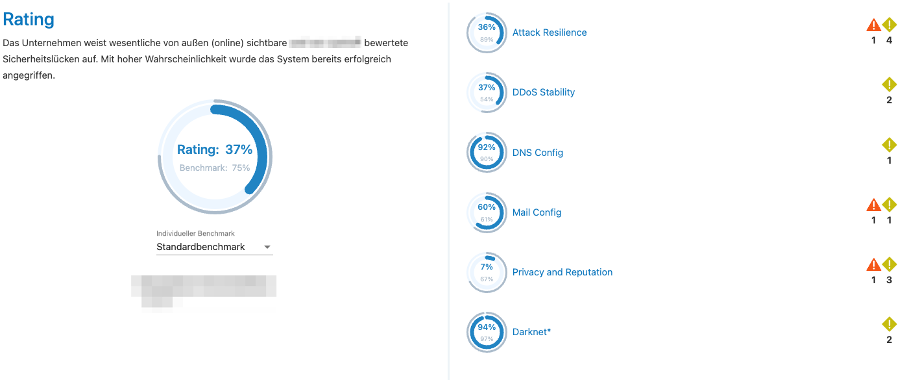
Screenshot of the results of an automated OSINT analysis
A short OSINT analysis of your own organization can reveal important information and is helpful in selecting the appropriate security measures. The However, it should always be used in the context of other security measures and taking into account the corresponding disadvantages such as lack of data quality. In order to achieve a sustainable effect through the use of the information, it is advisable to carry out regular penetration penetration tests and security assessments to test your own IT systems. systems. In this way, potential security problems can not only be identified identified but also verified. These steps are necessary, to subsequently initiate the rectification of these problems and to demonstrably demonstrably raise the level of security.
You would like to use OSINT data for your own cyber defense? Get in touch with contact the experts at CERTAINITY to develop a customized solution to and protect your organization as well as possible. We will gladly create an OSINT profile for you and advise you on the derivation and selection of possible security measures.
