
Do you know your risks, and can you assess them correctly?date: Jun 21, 2024
author: Emmanuel, Nowakowski-Gasser, Mag. MSc. PhD, Senior Consultant
The first part of this blog post series Do you know your assets? introduced the importance of threat modeling for manufacturing companies as well as the CERTAINITY modeling technique and the underlying metamodel. This modeling technique enables comprehensive modeling and assessment of threats and risks based on three levels of abstraction.
This blog post discusses the CERTAINITY method of threat modeling for manufacturing companies, based on the data flow of the modeling technique.
The following section describes the recommended method and shows how it enables the identification of threats as early as in the design phase of the development process, as well as the assessment and mitigation of risks. This helps manufacturing companies to develop more secure systems and enables them to achieve compliance with the European Cyber Resilience Act and IEC 62443 standards.
Modeling of Threats and Assessment of Risks
For threat modeling, the Failure Mode and Effects Analysis (FMEA) method is applied to the individual elements of the data flow model.
FMEA is a method for analyzing the risk of failures. It aims to avoid or mitigate failures in complex systems or processes by performing a systematic risk analysis. It helps manufacturing companies to recognize security or reliability deficiencies in the design phase and to design preventive or corrective measures.
For threat modeling with FMEA, the MITRE ATT&CK Matrix for ICS is used to analyze potential attack techniques on model elements. The matrix provides a knowledge base of tactics and techniques used by known threat actors in the industrial sector, based on actual observations. It structures the phases of the attack cycle and platforms used in a matrix, with tactics as columns and techniques as rows. Each technique includes examples, targets, mitigation techniques and attack detection methods.
Figure 1 shows the phases of the recommended threat modeling methodology for complex systems. The phases are described in detail in the following subsections.
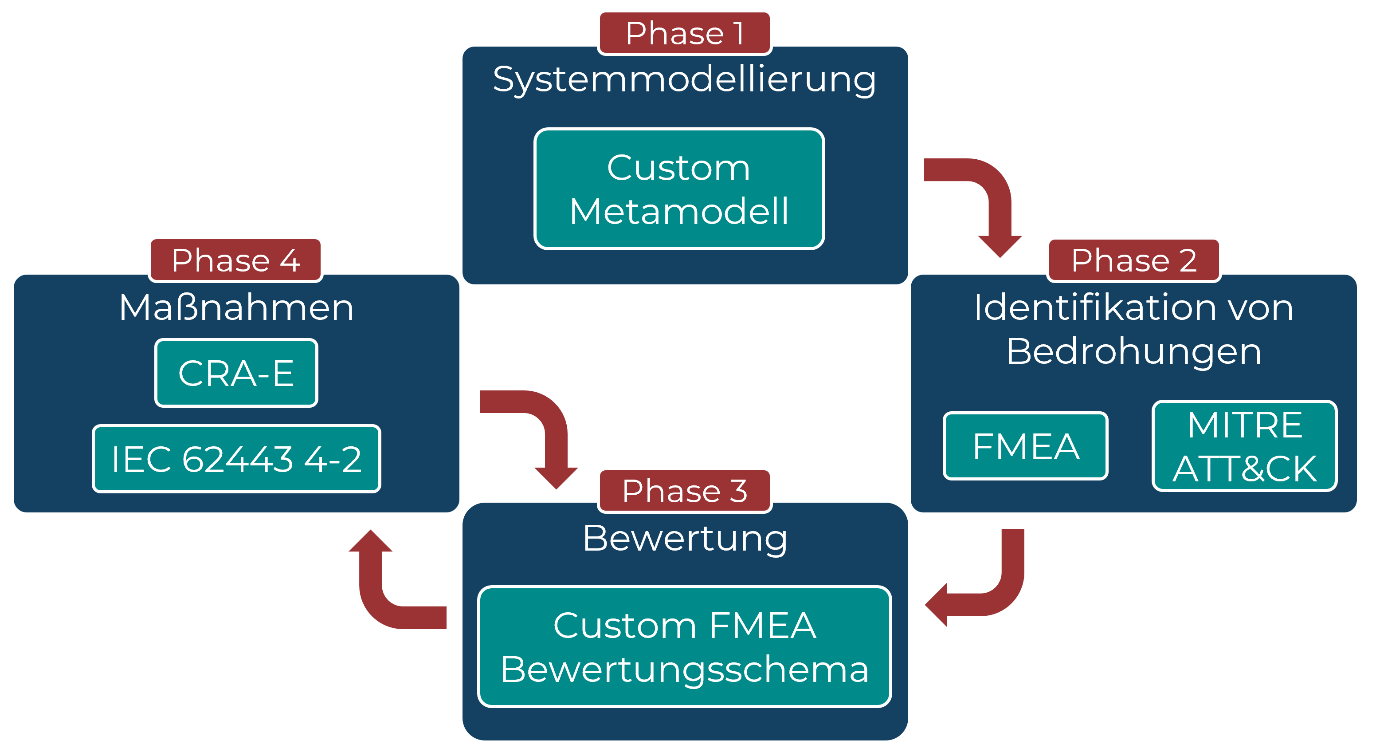
Figure 1: Phases of threat modeling.
PHASE 1:
In the first phase, the system is described and modeled using the CERTAINITY modeling technique (see Do you know your assets?). The metamodel must be adapted to the specific system. The data flow diagram helps to analyze system components and their connections for potential threats and to assess the impact of these threats. Phase 2 deals with the identification of threats and phase 3 with their evaluation.
PHASE 2:
In phase 2, potential failures, causes and consequences are analyzed. First, possible failures in the system are identified using the data flow diagram, the MITRE ATT&CK matrix for ICS and previous incidents. Relevant attack tactics from the MITRE ATT&CK matrix are evaluated and recorded in a table together with the corresponding techniques. Experiences from previous incidents are also considered. The potential impact of the failures on the user and the affected model elements are then added, along with ways of detecting vulnerability exploitation. Once the information is documented in the table, the next phase begins.
PHASE 3:
In the third phase, potential threats are evaluated and prioritized. In this context, the probability of occurrence (O), the severity (S) of the impact and the probability of detection (D) are relevant. The risk value (R) is determined by multiplying O, S and D. Each company can use its own rating scale. For illustration, a simple scale between 1 and 4 is suggested here for each criterion.
Criterion O indicates the probability of occurrence of the potential threat. The rating scale is based on the security levels (SL) of IEC 62443-3-3, which reflect the necessary capabilities of a threat actor. The probability of occurrence decreases with increasing complexity of the vulnerability.
Table 1 describes the different types of threat actors. The probability of occurrence depends on the means, resources, skills and motivation of the threat actor. In the case of the "careless user" threat actor, for example, the threat can be caused by a careless action.
| Threat actor | Means | Ressources | Skills | Motivation |
|---|---|---|---|---|
| State-sponsored | Sophisticated | High | ICS-specific | High |
| Hacker | Sophisticated | Medium | ICS-specific | Medium |
| Gelegenheitstäter | Simple | Low | Generic | Low |
| unvorsichtiger Nutzer | Simple | Low | Generic | Low |
Table 1: Threat actor profiles.
In Table 2, the probability of occurrence is assigned based on the threat actor profiles from Table 1 and the security levels of IEC 62443. The probability of occurrence increases the easier the vulnerability is to exploit.
| Threat Actor | probability of occurrence | Security Level |
|---|---|---|
| State-sponsored | 1 (very low) | SL 4 |
| Hacker | 2 (low) | SL 3 |
| Opportunist | 3 (medium) | SL 2 |
| Careless User | 4 (high) | SL 1 |
Table 2: Mapping of the threat actor profiles to the probability of occurrence and the IEC 62443 security levels.
Criterion S assesses the severity of the impact of a potential threat on a scale of 1 to 4. The severity levels are described in Table 3.
| Severity | Description |
|---|---|
| 1 (very low) | Impact on business is negligible, only isolated processes affected |
| 2 (low) | Limited impact on business, only a few processes are affected |
| 3 (medium) | Serious impact on the business, and many non-critical processes are also affected |
| 4 (high) | Serious impact on business, most processes are affected |
Table 3: Description of the impact severity.
The last criterion for the threat assessment is criterion D, which measures the probability of detection, i.e. the ability to detect or mitigate the exploitation of vulnerabilities. The assessment is carried out on a scale of 1 to 4, where 1 stands for very easy and 4 for difficult.
As a final step, the values for probability of occurrence, severity and probability of detection are multiplied together to determine the risk value of the threat. Table 4 shows possible consequences based on the calculated risk value, whereby the values for X and Y must be adjusted depending on the system criticality. The threats are prioritized according to their risk value. After evaluation and prioritization, the identified threats must be dealt with appropriately, which is done in phase 4.
| Risk Value | Failure Risk | Need for action | Security measures |
|---|---|---|---|
| R > Y | High | Urgent need for action | Must be formulated and implemented |
| X ≤ R ≤ Y | Medium | Need for action | Shall be formulated and implemented |
| 2 ≤ R ≤ X | Acceptable | No mandatory need foraction | Can be formulated and implemented |
| R = 1 | None | None | None |
Table 4: Depiction of the consequences in relation to the respective calculated risk (based on Orghandbuch)
PHASE 4:
In phase 4, security measures are defined to mitigate the identified risk scenarios. These measures are based on the risk value and the threat actor profiles. The risk value determines the urgency of treatment and supports prioritization. The threat actor profiles help to determine the appropriate security level in accordance with IEC 62443 and to derive appropriate security measures from the standards IEC 62443-3-3 for system security and IEC 62443-4-2 for secure product development. Security measures must be compliant with the European Cyber Resilience Act and the applicable regulatory requirements of the manufacturing company. Other standards can also be used if they ensure compliance with industry-specific laws and regulations.
Once the security measures have been defined, the risk is assessed after their implementation to determine the residual risk. This is determined by subtracting the risk after implementation from the original risk. As soon as an acceptable residual risk is reached, the measures are added to the table.
Threat modeling results in a living document that must be reviewed at least annually and updated in the event of security-relevant system changes. It ensures that many potential threats are already identified and dealt with in the design phase and is therefore crucial for a secure product development life cycle.
Details on the CERTAINITY method of threat modeling for manufacturing companies can be found in the next and final blog post in this series. There, the four phases of the methodology are explained step by step using an example.
CERTAINITY will be happy to support you in modeling your Industry 4.0, OT and IT landscape and in identifying, assessing and prioritizing your risks.
Make an individual appointment to discuss your questions and objectives with the experts at CERTAINITY. We will be happy to advise you on the choice of individual parameters to find the optimal approach to achieve your goals.
Please contact us at: sales@certainity.com
