
Is MFA the silver bullet against phishing?date: Nov 12, 2024
author: Yuri Gbur, Senior Security Consultant
Multi-factor authentication (MFA) is often presented as THE solution against phishing attacks, since a second factor (e.g. a temporary one-time password) cannot be reused by attackers. Many companies and software vendors therefore require their employees and customers to use MFA. Microsoft has also changed its requirements for MFA for many of its Azure cloud services since October 2024, enforcing the use of a second factor without the option of disabling it. More services will follow in early 2025 (https://azure.microsoft.com/en-us/blog/announcing-mandatory-multi-factor-authentication-for-azure-sign-in/).
Unfortunately, it is often misinterpreted that MFA is the comprehensive protection against phishing; namely attackers can access sensitive data through so-called “reverse-proxy phishing” despite MFA.
What is MFA
Multi-factor authentication (MFA) is a security concept in which a user must provide several “factors” when logging in. Such factors are usually something the user knows (e.g. a password), something the user owns (e.g. a mobile phone or Yubikey), something the user is (e.g. a fingerprint) or where he is (e.g. IP location). The best-known combination of two factors is a normal password and a one-time PIN (token), which is received or generated on a mobile device. The token represents the possession of the mobile device, can only be used once and is only valid for a limited time (e.g. 30 seconds).
Authentication on the web
Various requests on websites are sent back and forth -if the website requires authentication, you would (theoretically) send all factors with each request. This approach is of course not feasible with one-time PINs; already sending the password with each request would be insecure and cumbersome. That’s why modern websites use session cookies. After a successful login, the website assigns a unique session that identifies both the user and the authentication status for all subsequent requests. This session cookie is automatically sent by the browsers, so that the username and the password do not have to be transmitted upon each request. When logging out, or after a certain time, the cookie is invalidated and the session can no longer be used.
When MFA is in use, authentication works the same way. During login, all factors (e.g. password and one-time PIN) are entered and a session cookie is issued. This cookie now has an “MFA claim” and allows access to the protected functionality.
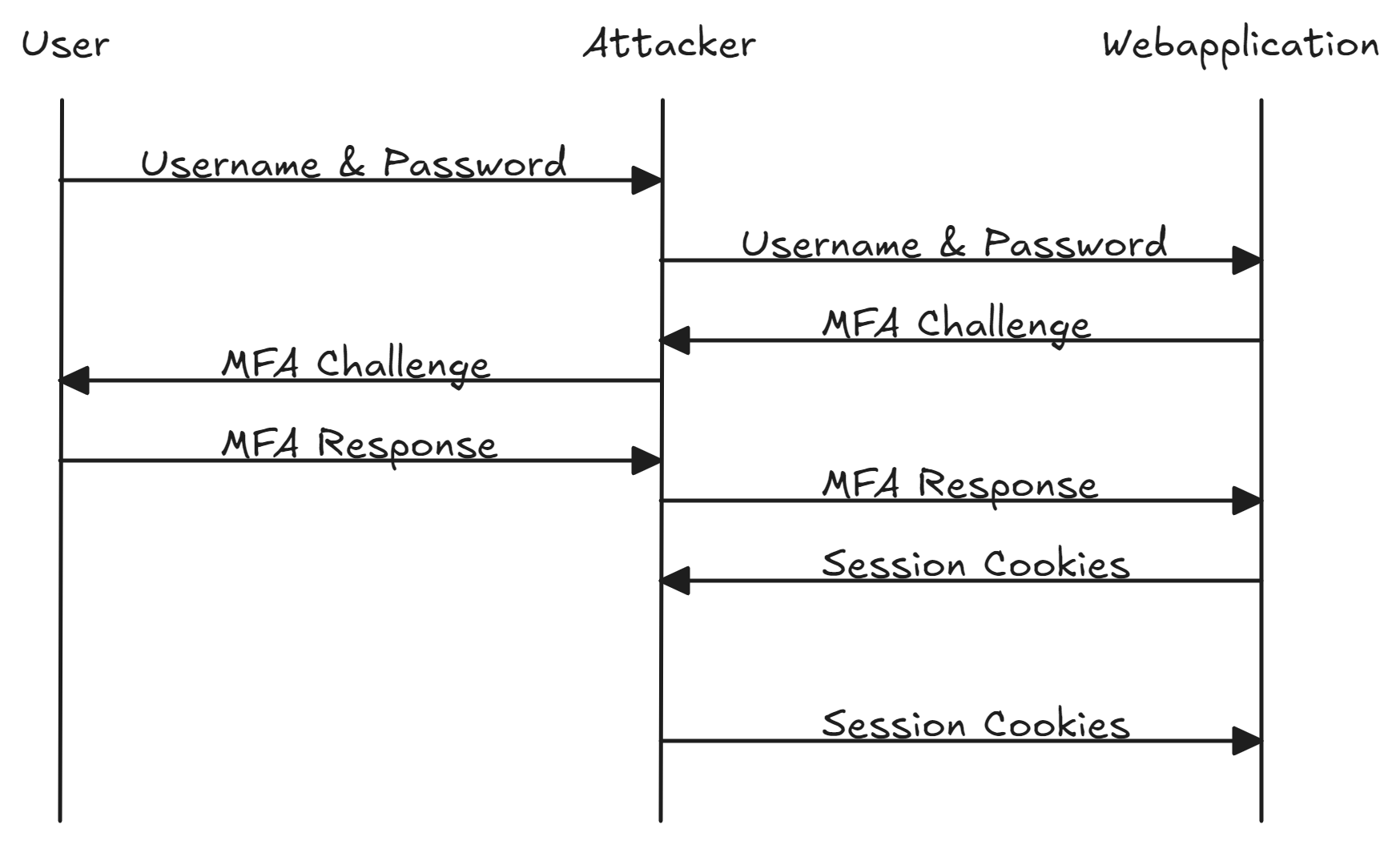
Phishing for MFA claim
When looking at the MFA authentication, the problem quickly becomes apparent. No matter how many factors are required, the issued session cookie allows the same access. Attackers can exploit this behavior in phishing attacks. While classic phishing attacks often clone websites, MFA phishing involves setting up a man-in-the-middle (MitM) position between the user and the legitimate web application. The attacker forwards all authentication factors to the login endpoint and intercepts the session cookies issued by the web application. The MitM attack is completely transparent to the user, who only sees the original login screen. Attackers can store the intercepted cookies locally in their browsers to then access the application.
The following video shows what such an attack looks like for M365 with Evilginx.
Limitations and solutions
Most applications require all factors to be re-entered for critical operations (e.g. resetting a password), even for active sessions. This is one of the most common measures against taking over an account completely via MFA phishing. Despite this limitation, session phishing is still extremely effective for initial attack paths. Access to internal information, emails and files is a goldmine for attackers. The information and internal sender addresses obtained can be used to build trust with other employees, which in turn greatly increases the chances of successfully executing malware.
Another approach is to use phishing-resistant MFA solutions such as FIDO2 security keys (e.g. Yubikey). Since the key is permanently linked to the domain origin for which it was registered, man-in-the-middle phishing via reverse proxies fails in many cases, as the attacker cannot imitate the original domain. Various websites also attempt to implement similar domain origin verification on the login pages using JavaScript code. Although such verification in the browser makes attacks more difficult, it should not be relied upon because attackers can analyze and manipulate the client-side JavaScript code to circumvent these mechanisms.
Employees are one of the most important pillars in the fight against phishing attacks. In addition to training courses on how to recognize phishing emails, at CERTAINITY we place particular emphasis on promoting a corporate culture in which no one has to be ashamed of becoming a victim of a phishing attack – because this can happen to anyone. Employees should feel safe reporting phishing incidents so that appropriate countermeasures can be quickly initiated. Our awareness page, which we link to after successful phishing simulations, can be viewed here: https://certainity.com/offensive/documents/phishing-awareness/
How can CERTAINITY help?
CERTAINITY offers comprehensive solutions to strengthen your company’s security against phishing:
- Standard phishing scenarios: Simulate targeted phishing attacks on your employees to analyze their reactions to threats, e.g. whether they click on links, enter passwords or inform the IT department.
- Awareness training: Our training courses teach your employees how to recognize phishing attempts and how to deal with them securely. This increases awareness of phishing attacks and establishes prevention strategies.
- Attack simulation and audits: CERTAINITY offers complete attack simulations, such as red team assessments and initial compromise audits. We also use the reverse proxy phishing for MFA logins described above to test your organization’s resilience against targeted and technically sophisticated phishing attacks and to identify vulnerabilities.
Please feel free to contact us (sales@certainity.com) at any time to discuss a customized approach that is specifically tailored to the requirements and issues of your organization.
