
Threat Modeling
Truly understanding cyber risks is a prerequisite in enabling informed decisions during development of software and digital products. By applying Threat Modeling techniques business analysts, development teams and the entire enterprise can gain insight into often hidden dependencies affecting the cyber security of their products and infrastructure. Proper threat modeling will ensure that critical design flaws are identified early.
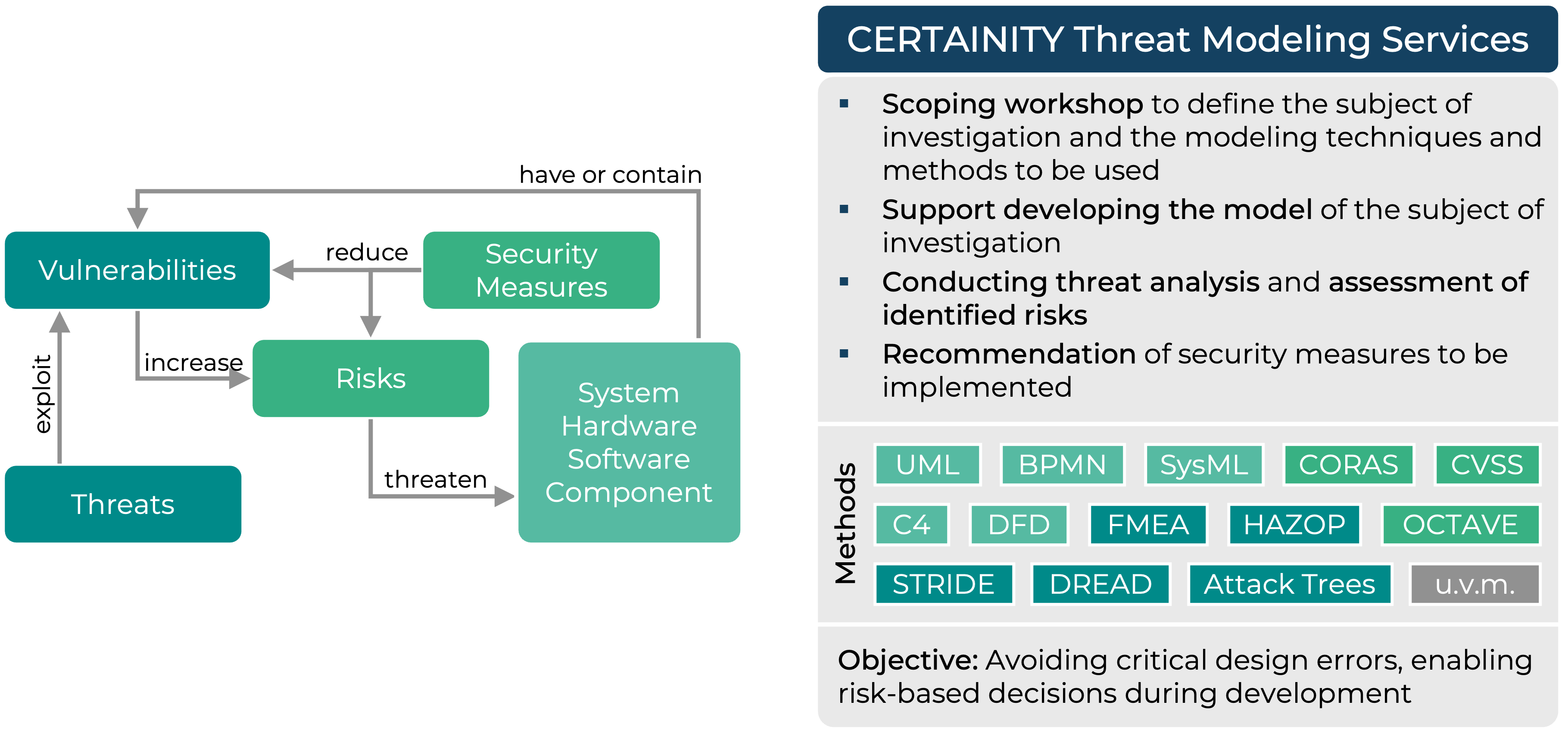
Our experienced security engineers apply the appropriate methods to create directly usable threat models, according to the investigated systems. We support FMEA, Attack Trees, STRIDE, CORAS and many more industry-proven risk modeling techniques. We always put the customer, their needs, and capabilities at the center of our consulting services. When needed, we help improve documentation quality to enable more formal analysis methods. Additionally, we provide trainings to enable our clients to establish a sustainable and independent threat modeling process. With our support, threat modeling becomes a vital part of your design process, development activities and service delivery.
Reduce the risk of critical design flaws and enable informed cyber risk decisions throughout product development with CERTAINITY’s Threat Modeling consulting services.
